If you are a little familiar with Computer Networking, then you must have a fair idea about the concept of SNMP. If not, don’t worry! We are here to deliver a detailed analysis of the topic. But, before we dive into our discussion, here are the major pointers that will be covered throughout this blog.
- What is SNMP?
- SNMP Port number
- How does SNMP work?
- SNMP monitoring tools
- Components of SNMP
- SNMP Versions
- SNMP Communication cycle
- What is SNMP Trap?
- Some basic SNMP Commands
What is SNMP?
What does SNMP mean? Simple Network Management Protocol or SNMP is a standard protocol. It is used to manage and communicate with the network devices that are interconnected through an IP. SNMP protocol is an Application layer protocol that was developed in the 1980s. It is an evident part of the TCP/IP protocol suite. Presently, the field of computer networking widely uses this protocol online.
It was presented by the IAB (Internet Architecture Board) in RFC1157. SNMP is highly useful in network administration as it gathers information related to network-connected devices and shares it amongst various software and hardware types. Now that you have a decent grip over the meaning of SNMP, let us move ahead to our next segment.
SNMP Port Number
SNMP runs on User Datagram Protocol or UDP Protocol port number 161/162. The port is basically a communication endpoint for SNMP. Take a look at the data given below to understand which process is allocated to which protocol.
When the manager and the agent communicate- UDP, 161
The manager receives a notification receipt - UDP, 162
A notification receipt - TLS/DTLS - 10162
A request receipt - TLS/DTLS - 10161
For a better understanding of the TCP and UDP protocols, check out our article here. Moving on, the next section explains to you the working of SNMP.
How does SNMP work?
There are ample activities that happen on a network all day. The users browse, download, transfer, and search, tons of information or data. SNMP in networking establishes communication with the entire network along with all the devices.
Additionally, the devices on SNMP are preconfigured. Once you enable the protocol, these devices further have the ability to gather the statistics related to their performance.
There are several network servers available on a network and each one of them will inhibit various MIB files. Moreover, the data monitored is stored in the device's MIB files.
SNMP sends SNMP GET requests to the network devices protocol data units. This in turn responds to these requests. These requests are completely tracked. Moreover, the network monitoring tools use these communication data to gather information from SNMP on the network.
So, what are these monitoring tools?
SNMP Monitoring Tools
There are several factors to take care of while operating the network. For instance, uptime, bandwidth-hog-free network, allocating ports interfaces or freeing them up. Network admins are available to manage these activities as well as the devices in any network.
It is essential to keep an eye while monitoring data and the devices. The task to monitor them is allocated to the network management tools.
Here are some of the most necessary tasks that SNMP monitoring tools perform:
- They help to manage the key performance metrics at two levels, namely, the device and interface levels.
- The tools manage as well as monitor the network devices automatically.
- They are also proficient in sending alerts, whenever any anomaly occurs.
How are these information snippets and the insights helpful to you? Well, The network admins are able to track and monitor the preferred means of SNMP network devices. They can also check the health of a network and take necessary steps to improvise it.
For more ease and comfort, the data is also available in several graphs and dashboards.
After obtaining an understanding of the subject, let us move forward to learn about the components of SNMP.
Components of SNMP
There are several essential components that demand an SNMP environment. Here is a list.
- SNMP Manager
- SNMP agent
- MIB
- Managed devices
- OID
SNMP Manager
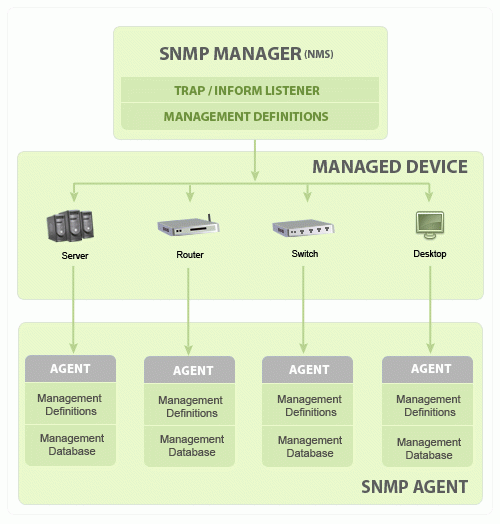
SNMP Manager is also known as NMS or Network Management Station. You can consider the SNMP manager as the central core system to monitor the entire network. It holds a vital place in the hierarchy overall.
An SNMP manager communicates with the SNMP agent about the events or anomalies that take place on the network.
The work of the SNMP manager is to ask queries to the SNMP agents about several issues that take place on the network. It receives responses against the queries and coordinates with the agent.
SNMP Agents
In simple words, it is software that sends responses to the SNMP manager‘s queries. It delivers the statistics or the information about the network to the manager. The SNMP agent also gathers the management information database locally from the device and delivers it to the manager.
Here are some of the essential functions of SNMP agents:
- It stores the management information as specified in the Management Information Base
- These agents also gather information about the local environment or more specifically, information about its local device
- They also have the capability to behave as a proxy for the non-SNMP manageable network node
- It is also possible for them to send a signal to the SNMP manager regarding any event
Take a look at the below showcasing the basic SNMP communication diagram to gain a better understanding.
MIB
MIB is the abbreviation for Management Information Base or Management Information Database.
As you have just read about SNMP agents, each agent has to maintain an information database wherein they describe the managed device parameters.
The SNMP manager accesses this database to further ask for some data or information from the SNMP agent. The manager also translates some data for the NMS or the Network Management System.
As you can see, there is a clear nexus between the SNMP manager and SNMP agent via the database. This shared database between both entities is known as Manager Information Base or Management Information Database.
These databases inhibit some statistics and values for several hardware nodes present on a network.
In a nutshell, these files are a set of questions asked by the SNMP Manager to the SNMP agent.
OID
OID is an abbreviation for the Object Identifier. The Management Information Base gathers information to manage network elements and consists of several managed objects that are termed OID.
Each such identifier is unique in its own way and reflects a particular characteristic of managed devices.
Additionally, there are two kinds of managed objects, Tabular and Scalar.
Tabular: means various object instances that are put together in MIB tables.
Scalar: a scalar object refers to a single object instance.
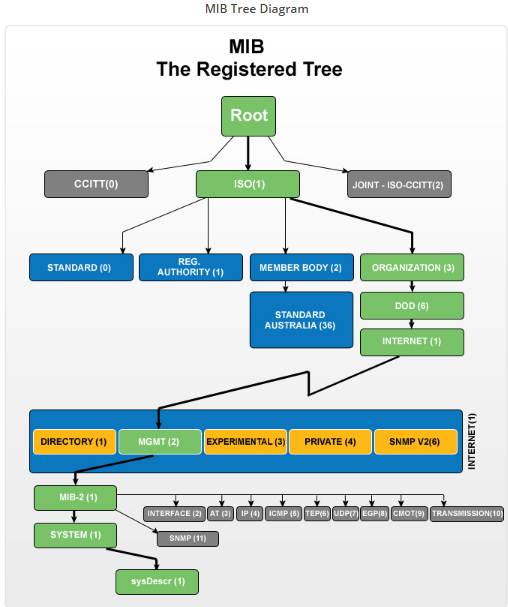
Moving on, every OID is placed in an organised hierarchy in the MIB. With individual variable identifiers, this hierarchy is displayed through a tree structure.
This is what the structure of a MIB tree looks like.
Now, let us quickly hop on to our next section that talks about different versions of SNMP.
Different versions of SNMP
There have been a good number of upgrades from the very inception of the SNMP protocol. But, SNMP protocol v1 and v2c are widely used versions.
A new version called SNMP protocol v3 is up in the market that excels when it comes to security. But this version is not successful yet in reaching a wide range of users in the market. Here is a little brief about all three versions of SNMP. Take a look.
SNMPv1: This version is defined in RFCs 1155 and 1157. It was the very initial version of the SNMP protocol.
SNMPv2: A lot of enhancements were made in this version of the SNMP protocol in several areas.
Areas including packet types, MIB structure elements etc. This version is defined in RFC 1901, RFC 1905, RFC 1906, RFC 2578.
Moving on to the latest and the last version of SNMP.
SNMPv3: it is the most secure version out of all the protocols. A lot of additions took place regarding the security factor. This protocol is defined by RFC 1905, RFC 1906, RFC 3411, RFC 3412, RFC 3414, RFC 3415.
SNMPv1, as well as SNMPv2c, are rich in community-based security. Whereas SNMPv2u and SNMP v3 are based on user-based security. Lastly, SNMP v2 is based on party-based security.
This version also supports the SNMP Engine ID identifier that is useful in the generation of a key for some authenticated messages.
Overall, SNMPv3 enhances the authentication and encryption of the network. Authentication is useful to ensure that the traps are read-only, whereas encryption ensures that the payload is not readable by some unauthorised users.
Now, another important terminology of SNMP protocol is the SNMP Trap.
SNMP Trap
An SNMP trap sends an SNMP message by enabling the SNMP agent to send a notification to the SNMP manager regarding some specific events or some anomaly.
There are several factors included in the SNMP trap protocols like OID and sysUpTime value. Talking about the format of such trap messages, there was a significant change in the second version, hence, the data units were called SNMPv2-Trap.
Besides, these messages are encoded. To decode them, you need a trap processor. Moving on, let us now discuss the basic process of SNMP communication.
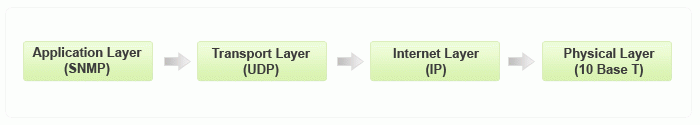
SNMP Communication
As you have read previously in this article, SNMP server is an evident part of the TCP/IP protocol. All the SNMP messages become part of the UDP or the User Datagram Protocol and are transferred to the Internet layer.
Here is a small representation of the process.
Now, our last section makes you familiar with the basic commands of SNMP.
Basic Commands of SNMP
Sending several messages or information is extremely easy with the help of SNMP protocol. This is a vital reason why it is widely popular and accepted. Here are some of the commands that make this exchange easier.
GET: any request that a manager sends to the managed device.
GET BULK: if you want to receive a huge amount of data from the MIB tables, use this command.
GET NEXT: this command is extremely similar to the GET operation, the only difference is that it fetches the next OID from the MIB tree.
SET: if the manager seeks to make any modification or wants to assign a value to the managed device, use this operation.
INFORM: it helps to avail a confirmation from the SNMP manager after messages are received.
TRAPS: traps are sent by the SNMP agents to the manager whenever any event or anomaly occurs.
RESPONSE: An SNMP manager sends a command in the form of values or signals. These actions are called RESPONSE commands.
Conclusion
In a nutshell, SNMP plays a vital role in the network protocol system. All the data and information are extremely useful for IT professionals to run the managed devices or applications. We hope that this article helps you to sort out all your ambiguities regarding SNMP protocol. Keep learning, keep treading ahead!
People also read: