When we want to hack a system, we need a specific exploit to take advantage of a certain operating system, service, or application vulnerabilities. There are many exploits available in the world. Remember that no specific exploit will allow you to exploit all systems. You need to find an exploit that will suit your target system. In such cases, the Exploit Database will help us. This article will guide you on installing SearchSploit in kali Linux and performing your task.
EDB is a project of Offensive Security, which developed the BackTrack and Linux kernel. This project is the ultimate archive of exploits, shellcodes, and security whitepapers. You can easily find various types of exploits, including:
- Remote exploits
- Web Application exploits
- Local and Privilege Escalation exploits
- Denial of Service exploits
- Shellcode exploits
Then, if you feel it will work for your target, you can simply copy and paste it into Kali for your attack. Exploits are categorized by platform, type, language, port, etc., in this project.
To deepen your understanding of this powerful OS, explore our comprehensive guide on What is Kali Linux, where we cover its features, uses, and why it's a go-to choice for cybersecurity professionals.
What is SearchSploit?
SearchSploit is a command-line search tool for Exploit-DB that allows you to take a copy of the Exploit Database. SearchSploit allows you to perform offline searches through your local repository copy. This capability is especially useful for security assessments on networks without Internet access.
For optimal performance and access to the latest exploit database, make sure your Kali Linux is up to date. Learn more about how to update Kali Linux to keep your system prepared for comprehensive security assessments.
How to install SearchSploit in Kali Linux? [A Guideline to use SearchSploit]
To install SearchSploit, you can use the git clone method to directly clone the SearchSploit into your kali from the GitHub repository.
git clone https://github.com/offensive-security/exploit-database.git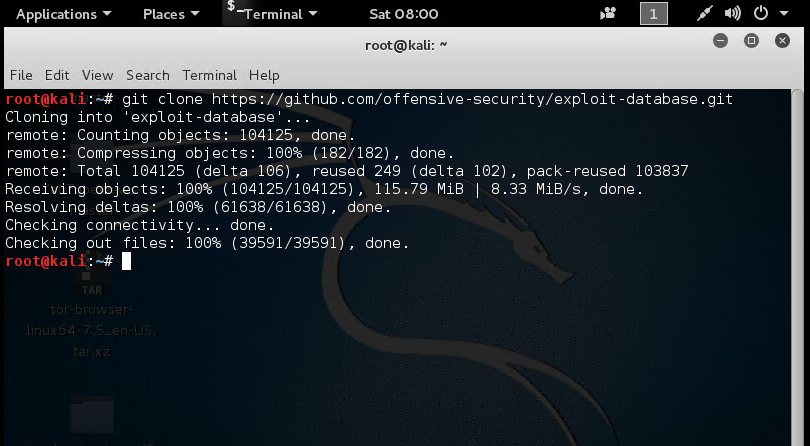
Then update your system and install this tool using the following command:
apt update && apt -y install exploitdb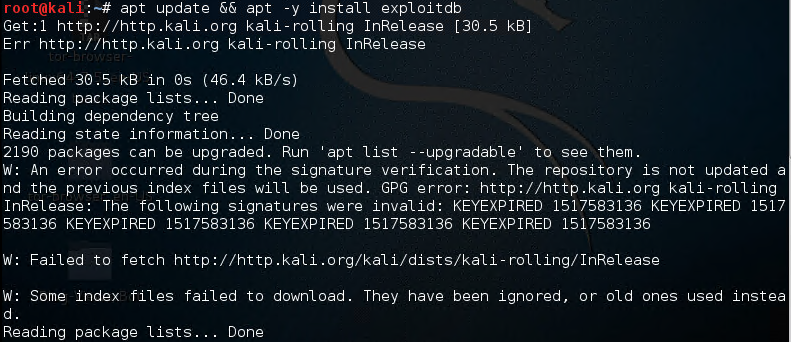
How to use SearchSploit?
By using " -h ", you can see all the features and options that are available to you:
root @ kali: ~ # searchsploit -h
Usage: searchsploit [options] term1 [term2] ... [termN]
==========
Examples
==========
searchsploit afd windows local
searchsploit -t oracle windows
searchsploit -p 39446
searchsploit linux kernel 3.2 --exclude = "(PoC) | / dos /"
For more examples, see the manual: https://www.exploit-db.com/searchsploit/
== =======
Options
=========
-c, -case [Term] Perform a case-sensitive search (Default is inSEnsITiVe).
-e, --exact [Term] Perform an EXACT match on the exploit title (Default is AND) [Implies "-t"].
-h, --help Show this help screen.
-j, --json [Term] Show result in JSON format.
-m, --mirror [EDB-ID] Mirror (aka copies) an exploit to the current working directory.
-o, --overflow [Term] Exploit titles are allowed to overflow their columns.
-p, --path [EDB-ID] Show the full path to an exploit (and also copy the path to the clipboard if possible).
-t, --title [Term] Search JUST the exploit title (Default is the title AND the file's path).
-u, --update Check for and install any exploitdb package updates (deb or git).
-w, --www [Term] Show URLs to Exploit-DB.com rather than the local path.
-x, --examine [EDB-ID] Examine (aka opens) the exploit using $ PAGER.
--colour Disable color highlighting in search results.
- Display the EDB-ID value rather than local path.
--nmap [file.xml] Checks all results in Nmap's XML output with service version (eg: nmap -sV -oX file.xml).
Use "-v" (verbose) to try even more combinations
--exclude = "term" Remove values from results. By using "|" You can chain multiple values.
eg --exclude = "term1 | term2 | term3".
=======
Notes
=======
* You can use any number of search terms.
* Search terms are not case-sensitive (by default), and ordering is irrelevant.
* Use '-c' if you want to reduce results by case-sensitive search.
* And / Or '-e' if you want to filter results by using exact match.
* Use '-t' to exclude the file's path to filter the search results.
* Remove false positives (especially when searching using numbers - ie versions).
* When updating or displaying help, search terms will be ignored.
root @ kali: ~ #
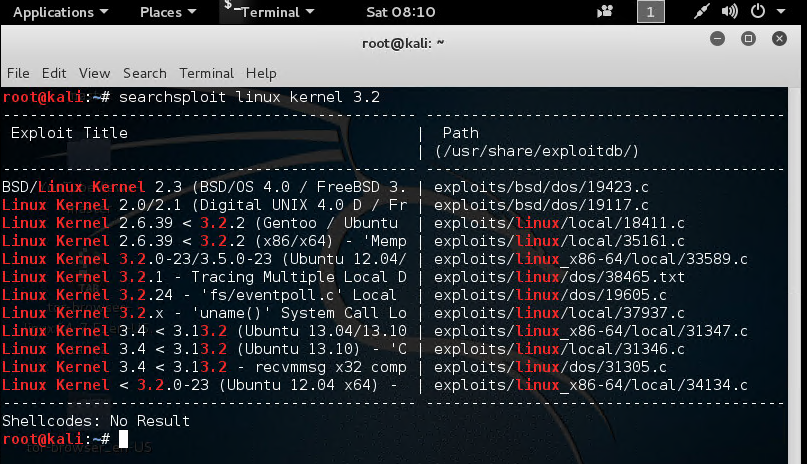
Type this command to search for Linux Kernel 3.2:
searchsploit linux kernel 3.2It will list all the exploits related to Linux Kernel.
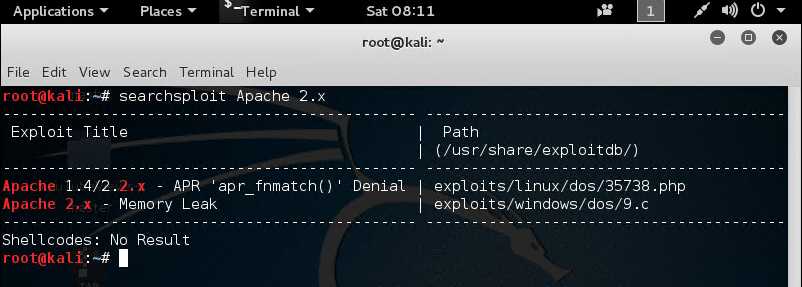
You can type " searchsploit Apache 2.x " to see these exploits related to Apache 2.x:
How to Keep SearchSploit Up-to-Date?
To update SearchSploit, all you need to do is run the following Linux command:
$ searchsploit -u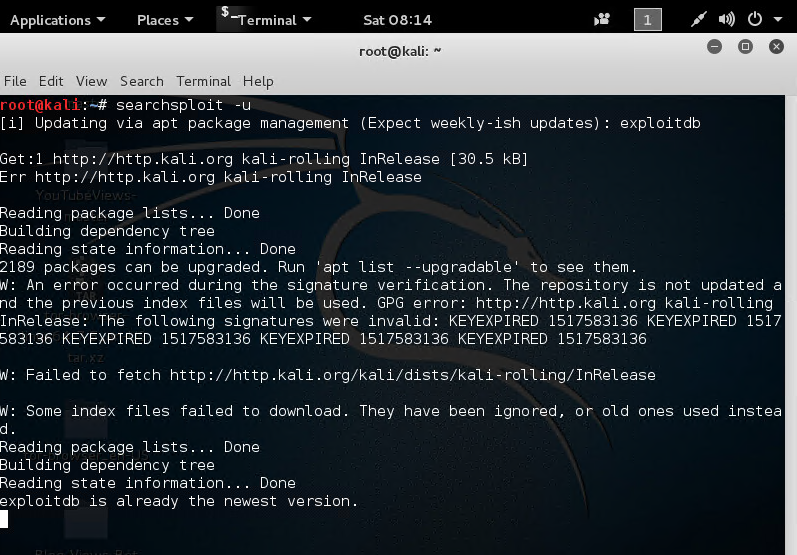
Conclusions
Congratulations! You have learned how to install SearchSploit on Kali Linux vps. Feel free to comment here if you encounter any problems during the installation. We will help you to solve the issue. You can also buy linux vps to practice it on a routine basis.
If you're looking to further enhance your Kali Linux setup, consider checking out our guide on installing OpenVAS in Kali Linux for advanced vulnerability scanning and network security analysis.
People Are Also Reading:
![How to Install SearchSploit on Kali Linux? [User SearchSploit] How to Install SearchSploit on Kali Linux? [User SearchSploit]](
https://1gbits.com/cdn-cgi/image/width=827,quality=80,format=auto/https://s3.1gbits.com/blog/2021/06/how-to-install-searchsploit-in-kali-linux325-847xAuto.jpg
)



![What Is Cold Data Storage? ❄️ [2026 Guide] What Is Cold Data Storage? ❄️ [2026 Guide]](https://1gbits.com/cdn-cgi/image//https://s3.1gbits.com/blog/2026/02/what-is-cold-data-storage-750xAuto.webp)