Linux logs are essential tools for understanding and troubleshooting system operations, providing insights into system performance, user activities, and application behavior. Whether you're looking to check Linux logs for debugging, analyzing issues, or enhancing security, these logs are a treasure trove of information. You can learn how to read Linux logs to investigate specific events or use commands like tail Linux logs for real-time monitoring. Logs like crontab Linux logs track scheduled tasks, while ssh Linux logs and docker Linux logs detail remote connections and container activity. To optimize log management, it's crucial to know where Linux logs are stored, from the Linux logs location to analyzing logs for authentication or boot events. Tools like Linux log analyzers and log aggregation solutions simplify complex log analysis. Whether clearing Linux logs or diving into Linux logs before a reboot, understanding logs is vital for system administrators and developers alike. If You need Linux VPS, visit Linux VPS Hosting page.
What are Linux Logs?
Linux logs are detailed records generated by a Linux system that provide information about system activities, application behavior, and user interactions. They serve as a valuable tool for troubleshooting, performance monitoring, and security analysis. Whether you're managing a personal device or a large server, understanding and utilizing Linux logs effectively is critical for maintaining system health and ensuring smooth operations.
At their core, Linux logs contain entries about events and processes that occur within the system. They are stored in specific locations, with /var/log being the primary directory. To address the common question, "Where are Linux logs stored?" the answer lies in this centralized location, which houses logs for system components, applications, and services. For instance, Linux logs for Apache web servers can be found in /var/log/apache2/ on Debian-based systems or /var/log/httpd/ on Red Hat-based systems.
Linux logs also track user activities and system commands. Using tools or commands, administrators can review a detailed history of actions, including Linux log all commands executed by users. This is particularly useful for auditing purposes. To improve security, Linux log authentication entries provide insights into login attempts and potential unauthorized access. Additionally, steam Linux logs can help gamers diagnose issues with the Steam client, while crontab Linux logs reveal the execution status of scheduled tasks.
For effective log management, learning how to read Linux logs is a crucial skill. Commands like cat, less, and tail allow users to view logs directly. For example, using tail Linux logs enables real-time monitoring of a log file's most recent entries, which is helpful when debugging ongoing issues. Advanced users often rely on Linux log analysis tools to process and interpret large volumes of data. These tools, such as Graylog or the ELK Stack, offer powerful Linux log aggregation and visualization features.
Managing Linux logs also includes maintenance tasks like ensuring logs do not consume excessive storage space. To achieve this, you can clear Linux logs using commands like logrotate or manual deletion. However, be cautious when performing this operation, as deleting important logs without backup can hinder future troubleshooting efforts.
Logs also play a vital role in understanding system behavior before and after specific events. For example, analyzing Linux logs before reboot can help pinpoint errors or warnings that led to a crash. Similarly, Linux log boot records provide details about the system startup process, helping identify issues with initialization.
When working with logs, permissions are a key consideration. Some tasks may require elevated privileges, so users might need to access Linux logs as root. However, for non-critical analysis, accessing Linux logs as a user is often sufficient.
Linux logs are a gateway to understanding system performance and reliability. Whether you're investigating Linux log all commands executed, analyzing Linux logs Apache errors, or using Linux log aggregation for a unified view, they provide the necessary information to diagnose, monitor, and improve your system’s operations. With a systematic approach to Linux log analysis, administrators can ensure optimized performance and robust security for any Linux environment.
How can Linux Logs Help?
Linux logs are indispensable tools for system administrators, developers, and security professionals, offering detailed insights into a system’s behavior and performance. They provide critical information about processes, user activities, application errors, and security events. By effectively using Linux logs, you can troubleshoot problems, optimize performance, and ensure the stability and security of your system. Let’s explore the various ways Linux logs can help and how they can be leveraged effectively.
Linux logs serve as a record of everything happening on your system. They detail system events, startup sequences, and shutdown processes. For instance, Linux log boot files capture all the information related to the system’s initialization, including loaded services and potential errors during startup. Similarly, Linux logs before reboot allow you to identify issues that might have led to a system failure or prompted a restart. By analyzing these logs, you can pinpoint recurring issues and address them proactively.
Troubleshooting Errors
One of the most common uses of Linux logs is diagnosing and resolving system errors. Whether an application is crashing or a service isn’t starting, the logs can provide detailed error messages and timestamps. For example, by accessing Linux logs as root, administrators can view privileged information that may not be accessible to standard users. These logs often include critical system files, such as /var/log/syslog or /var/log/messages, which are essential for understanding system-wide errors.
For less sensitive tasks, you can access Linux logs as a user. This approach is safer for regular analysis and avoids the risks associated with elevated privileges. Tools like less, cat, or graphical interfaces make it easy to explore log files for troubleshooting purposes.
Tracking User Activities and Commands
Linux logs are vital for auditing and monitoring user activities. Using commands like history in conjunction with logging tools, you can examine Linux log all commands executed by users on the system. This feature is particularly useful for identifying unauthorized changes or tracking specific activities performed by users. For example, developers can review command logs to debug scripts, while security teams can audit activities for compliance purposes.
Enhancing Security
Security monitoring is one of the most critical functions of Linux logs. Logs like /var/log/auth.log provide Linux log authentication details, including successful and failed login attempts. These logs can help detect potential brute-force attacks or unauthorized access to your system. By analyzing authentication logs, you can identify suspicious patterns and strengthen your security measures, such as implementing stricter password policies or enabling two-factor authentication.
Centralized Log Management with Aggregation
For larger environments, managing individual log files across multiple servers can be overwhelming. Linux log aggregation tools like the ELK Stack (Elasticsearch, Logstash, Kibana) or Graylog enable centralized collection and analysis of logs. By aggregating logs from multiple sources, you can create a unified view of your system's behavior, making it easier to identify trends and anomalies. These tools often include visualization features, allowing you to monitor system performance through dashboards and alerts.
Proactive Maintenance
Regularly analyzing Linux logs can help in proactive system maintenance. By monitoring system health and performance indicators, you can detect potential issues before they escalate. For instance, disk usage warnings in logs can alert you to free up space before running out of storage. Additionally, reviewing Linux logs before reboot can help prevent unnecessary downtime by identifying unresolved issues.
Improving System Efficiency
Logs aren’t just about fixing problems—they’re also about optimization. By analyzing resource usage patterns and performance metrics, Linux logs help administrators fine-tune their systems. For example, if certain services are consuming excessive CPU or memory, the logs can highlight these inefficiencies, enabling corrective actions.
Facilitating Compliance and Audits
For organizations subject to regulatory standards, Linux logs play a vital role in maintaining compliance. Logs provide detailed records of user actions, system changes, and security incidents, which are often required during audits. With tools to analyze Linux log all commands and authentication logs, administrators can demonstrate adherence to security and operational policies.
Accessing Logs Safely
To make the most of Linux logs, it’s important to manage access carefully. While accessing Linux log as root provides unrestricted visibility, it should only be used when necessary, as it poses risks if mishandled. For day-to-day monitoring, accessing Linux log as user is sufficient and minimizes the chance of accidental changes to critical system files.
Practical Applications in Real Scenarios
Linux logs are invaluable across a range of scenarios. For example:
-
Debugging System Startups: By reviewing Linux log boot files, you can identify services that failed to start and take corrective actions.
-
Detecting Intrusions: Analyzing Linux log authentication entries helps detect unauthorized login attempts and implement stronger security measures.
-
Tracking Changes: Linux log all commands executed by administrators allow you to trace system modifications, making it easier to revert or document changes.
-
Aggregating Logs for Clarity: Using Linux log aggregation tools consolidates data from multiple servers, simplifying complex log analysis tasks.
Linux logs are powerful tools that provide insights into system operations, performance, and security. Whether you’re accessing Linux log as root for in-depth troubleshooting, using Linux log aggregation tools for centralized monitoring, or analyzing Linux log authentication entries to enhance security, these logs are essential for system management. From tracking Linux log all commands to diagnosing Linux log boot issues, leveraging logs effectively ensures that your Linux environment remains efficient, secure, and reliable.
Where to find Linux Logs?
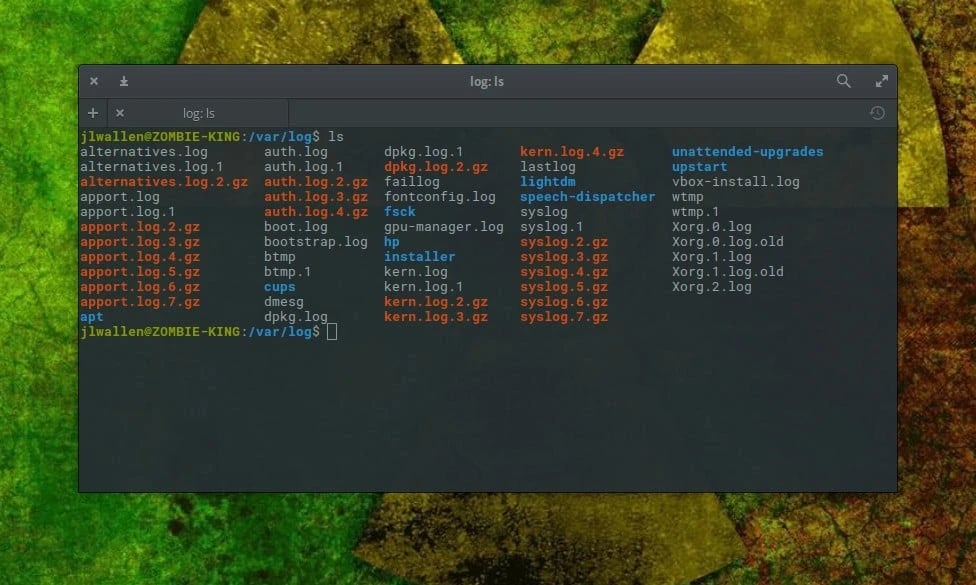
Linux logs are essential for monitoring, troubleshooting, and maintaining system performance and security. These logs capture a wide range of information, from system events to application-specific activities. Knowing where to find Linux logs, how to view them, and understanding their types can significantly enhance your ability to manage a Linux system efficiently.
Linux Logs Location
Most Linux logs are stored in the /var/log/ directory, which serves as a central repository for system and application logs. Within this directory, you’ll find various files, each dedicated to specific log types. For instance:
-
/var/log/syslog or /var/log/messages: These files store general system activity logs and are crucial for troubleshooting common issues.
-
/var/log/auth.log: Contains authentication-related logs, including login attempts and SSH activities.
-
/var/log/kern.log: Records kernel messages, useful for debugging hardware or kernel issues.
-
/var/log/boot.log: Tracks the system boot process.
-
/var/log/dmesg: Provides kernel ring buffer messages, including hardware detection during boot.
By understanding the Linux logs location, you can quickly navigate to the required files for specific troubleshooting needs.
Types of Logs in Linux
Linux logs are broadly categorized based on their purpose and the type of data they record. Some common types include:
-
System Logs: These cover system-level activities such as boot processes, kernel operations, and general system behavior. Files like /var/log/syslog and /var/log/messages fall into this category.
-
Authentication Logs: Found in /var/log/auth.log, these logs detail login attempts, user authentications, and potential security breaches.
-
Application Logs: These logs are generated by applications like Apache, NGINX, or MySQL, often stored in subdirectories under /var/log/.
-
Network Logs: These track network-related activities, including connections and firewall events. For example, logs for IPTables are often stored in /var/log/iptables.log or integrated with system logs.
-
Event Logs: Cover specific services or daemons, such as cron jobs, stored in files like /var/log/cron.
How to View Log Files in Linux Command Line
To View log file in Linux command, you can use several commands depending on the type of analysis you need. Here are a few common methods to view Linux network logs. Also read How to Monitor Linux Network Traffic, and How to use Linux.
-
Using cat: Displays the entire content of a log file.
-
cat /var/log/syslog
-
Using less: Allows scrolling through large log files.
-
less /var/log/auth.log
-
Using tail: Shows the last few lines of a log file, useful for checking recent events.
-
tail /var/log/messages
-
Using grep: Filters logs for specific keywords or patterns.
-
grep "error" /var/log/syslog
These commands make it easy to navigate and analyze logs in real time or retrospectively.
Linux Log Command
The journalctl command is a powerful utility for managing system logs stored by the systemd journal. It enables viewing, filtering, and exporting logs:
-
Display all logs:
-
journalctl
-
View logs for a specific service:
-
journalctl -u apache2.service
-
Show logs from the current boot session:
-
journalctl -b
The journalctl command simplifies working with logs and provides advanced filtering options.
How to Check Error Logs in Linux
Error logs are crucial for identifying and fixing issues in a Linux system. Depending on the source of the error, you can check different log files:
-
System Errors: Look in /var/log/syslog or /var/log/messages.
-
grep "error" /var/log/syslog
-
Authentication Errors: Check /var/log/auth.log.
-
Application Errors: Review application-specific logs, such as /var/log/apache2/error.log for Apache.
Using tools like grep or journalctl with error-related keywords can quickly help locate issues.
How to View Live Logs in Linux Command Line
To monitor logs in real-time, you can use the tail command with the -f option:
tail -f /var/log/syslog
This command continuously displays new log entries as they are written. For more advanced live monitoring, tools like less +F or journalctl -f can be used.
/var/log/messages in Linux
The /var/log/messages file is one of the most commonly used logs in Linux. It contains general system activity messages, including service starts, shutdowns, and errors. It’s an essential log for troubleshooting system-wide issues. However, some distributions like Ubuntu replace /var/log/messages with /var/log/syslog for similar functionality.
Linux Network Logs
Network logs provide valuable insights into network-related activities, such as connection attempts, packet filtering, and firewall rules. These logs are often found in /var/log/syslog or dedicated files like /var/log/iptables.log. For live monitoring, you can use:
sudo tail -f /var/log/syslog | grep "network"
This allows real-time tracking of network events.
Understanding the Linux logs location and how to view them is crucial for effective system management. By mastering tools like journalctl, tail, and grep, you can quickly access and analyze logs for various purposes, from troubleshooting errors to monitoring live events. Whether checking /var/log/messages in Linux or performing advanced Linux log aggregation, these logs empower administrators to maintain a robust, secure, and efficient system.
How to View Linux Logs?
Viewing Linux logs is an essential task for system administrators and users who need to monitor system activities, debug issues, or maintain security. Linux logs record various events, such as system operations, authentication attempts, application activities, and network traffic. This guide explores how to view Linux logs, the tools and commands available, and best practices for efficient log management.
Before diving into the tools and techniques, it’s important to understand the basics of Linux logs. These logs are text-based records of events generated by the system, kernel, applications, and services. They provide insights into the functioning of the system and help troubleshoot errors.
Most Linux logs are stored in the /var/log/ directory, which contains files like:
-
/var/log/syslog or /var/log/messages: General system and application logs.
-
/var/log/auth.log: Authentication logs, including login attempts and failures.
-
/var/log/kern.log: Kernel-specific logs.
-
/var/log/dmesg: Boot and hardware detection logs.
-
/var/log/boot.log: Logs related to the system boot process.
There are several commands and tools available to view Linux logs effectively. Below are the most common methods:
1. Viewing Logs with cat
The cat command displays the entire contents of a log file. This method is useful for small files.
Example:
cat /var/log/syslog
2. Using less or more for Large Logs
For larger log files, less and more allow scrolling through the content line by line or page by page.
less /var/log/auth.log
Press q to exit the less viewer.
3. Checking Recent Logs with tail
The tail command shows the last few lines of a log file. It’s useful for viewing recent events or monitoring logs in real time.
tail /var/log/messages
For real-time updates, use the -f flag:
tail -f /var/log/syslog
4. Filtering Logs with grep
To search for specific information within logs, grep is an invaluable tool. It helps locate keywords or patterns in log files.
grep "error" /var/log/syslog
You can combine grep with tail for live filtering:
tail -f /var/log/syslog | grep "error"
5. Viewing Logs with journalctl
For systems running systemd, the journalctl command provides access to logs stored by the system journal. It offers advanced filtering and search capabilities.
-
View all logs:
journalctl
-
View logs for a specific service:
journalctl -u ssh.service
-
View logs from the current boot:
journalctl -b
For real-time logs:
journalctl -f
6. Checking Logs Using Graphical Tools
For those who prefer graphical interfaces, tools like Logwatch, KSystemLog, or Logrotate provide user-friendly ways to view and manage logs.
How to Check Error Logs in Linux
Error logs are vital for identifying issues in the system or applications. Use grep to search for errors in system logs:
grep "error" /var/log/syslog
For application-specific errors, navigate to the respective log file. For example, to view Apache errors:
cat /var/log/apache2/error.log
Most Important Linux Logs
1. System Logs (/var/log/syslog or /var/log/messages)
The system log, typically located in /var/log/syslog or /var/log/messages (depending on the distribution), is one of the most important logs on a Linux system. It captures general system activities, including kernel messages, user processes, and system events. These logs contain information about the operation of the system, which can be valuable for debugging system-wide issues or identifying potential security breaches.
-
What it contains: General system events, boot sequences, errors, warnings, and debugging information.
-
Why it’s important: It provides insights into the overall health of the system and records crucial information that helps in diagnosing both hardware and software problems.
Example command to view syslog:
less /var/log/syslog
2. Authentication Logs (/var/log/auth.log)
Authentication logs, found in /var/log/auth.log on Debian-based systems or /var/log/secure on Red Hat-based systems, record authentication-related events such as login attempts, sudo commands, and SSH sessions. Monitoring this log is essential for ensuring that unauthorized access attempts are detected early.
-
What it contains: Login and logout events, failed and successful authentication attempts, sudo command usage, SSH access attempts.
-
Why it’s important: It helps to track and prevent unauthorized access to the system. Monitoring authentication logs is essential for security audits and detecting brute-force attacks, suspicious login attempts, or privilege escalation.
Example command to view auth.log:
less /var/log/auth.log
3. Kernel Logs (/var/log/kern.log)
The kernel log, stored in /var/log/kern.log, records messages generated by the Linux kernel. This log contains critical information about hardware detection, driver issues, and kernel panics. It is especially useful when diagnosing hardware failures or kernel-related problems.
-
What it contains: Kernel messages related to hardware events, driver loading, system crashes, and other low-level issues.
-
Why it’s important: If the system is experiencing hardware failures or crashes, kernel logs can help pinpoint the root cause by providing specific kernel-level error messages.
Example command to view kern.log:
less /var/log/kern.log
4. Boot Logs (/var/log/boot.log)
Boot logs, found in /var/log/boot.log, capture messages generated during the system boot process. This log provides valuable information regarding the initialization of system services and hardware detection. Any issues that occur during boot will be logged here, making it crucial for diagnosing boot-related problems.
-
What it contains: Messages from the boot process, including the initialization of services, hardware detection, and errors during startup.
-
Why it’s important: If a system fails to boot or encounters issues during boot, the boot log provides valuable clues to the underlying problem.
Example command to view boot.log:
less /var/log/boot.log
5. Application Logs (/var/log/[application_name])
Many applications, including web servers, databases, and system services, maintain their own log files to record their activities. For example, Apache’s access logs are stored in /var/log/apache2/access.log and error logs in /var/log/apache2/error.log. Similarly, MySQL or other database systems maintain their own logs. These logs are useful for monitoring application performance, tracking errors, and understanding user interactions.
-
What it contains: Application-specific events, errors, warnings, user interactions, and performance metrics.
-
Why it’s important: They help troubleshoot application-specific issues such as database errors, web server failures, or failed user requests.
Example command to view Apache logs:
less /var/log/apache2/access.log
6. Mail Logs (/var/log/mail.log or /var/log/maillog)
Mail logs, usually located in /var/log/mail.log or /var/log/maillog, track email system activity. This includes information about sent and received mail, mail server errors, and issues related to the email queue.
-
What it contains: Mail transfer agent (MTA) activities, delivery successes or failures, email-related errors, spam filtering logs.
-
Why it’s important: For mail server administrators, mail logs are essential for troubleshooting delivery issues, monitoring spam filtering, and ensuring that the mail system is functioning correctly.
Example command to view mail logs:
less /var/log/mail.log
7. X11 Logs (/var/log/Xorg.0.log)
X11 logs, stored in /var/log/Xorg.0.log, track events related to the X Window System (the graphical user interface for Linux). These logs record details about the X server’s initialization, graphical issues, and hardware compatibility with display drivers.
-
What it contains: Information about the X server's operation, hardware detection, and errors related to the graphical environment.
-
Why it’s important: For troubleshooting graphical issues such as display problems, screen resolution, or driver failures, X11 logs provide insights into what went wrong during the X server’s initialization.
Example command to view Xorg log:
less /var/log/Xorg.0.log
8. CRON Logs (/var/log/cron)
Cron jobs are scheduled tasks that run at specific intervals on Linux systems. The cron log, located in /var/log/cron or /var/log/cron.log, records the execution of these scheduled tasks. It helps verify whether cron jobs executed as expected and can provide information about any issues or failures.
-
What it contains: Information about cron job execution, including the time and status of each job.
-
Why it’s important: Monitoring cron logs is essential for ensuring that automated tasks run successfully, such as backups, updates, or other system maintenance tasks.
Example command to view cron logs:
less /var/log/cron
Conclusion
In conclusion, Linux logs are crucial for monitoring system performance, diagnosing issues, and ensuring security. By regularly reviewing logs such as system, authentication, and kernel logs, users can proactively address potential problems, optimize system operations, and enhance security. Mastering Linux logs is essential for efficient system management and maintaining a stable, secure environment.





![What Is Cold Data Storage? ❄️ [2026 Guide] What Is Cold Data Storage? ❄️ [2026 Guide]](https://1gbits.com/cdn-cgi/image//https://s3.1gbits.com/blog/2026/02/what-is-cold-data-storage-750xAuto.webp)