Nowadays, containers are the core of modern software infrastructures. In this field, there are two main technologies, which are system containers (LXC) and application containers (Docker). To begin with, they both provide a way to isolate applications and services, but their design and scenarios for which they are intended vary. We go through the differences of each technology in terms of their architecture, performance, security, and use case in this article from MonoVm to facilitate your decision in picking the suitable tool for your project.
Introduction to Docker and LXC
The root difference between Docker and LXC lies in their isolation philosophy. This philosophical distinction shapes all other aspects of their architecture and use cases.
What is Docker?
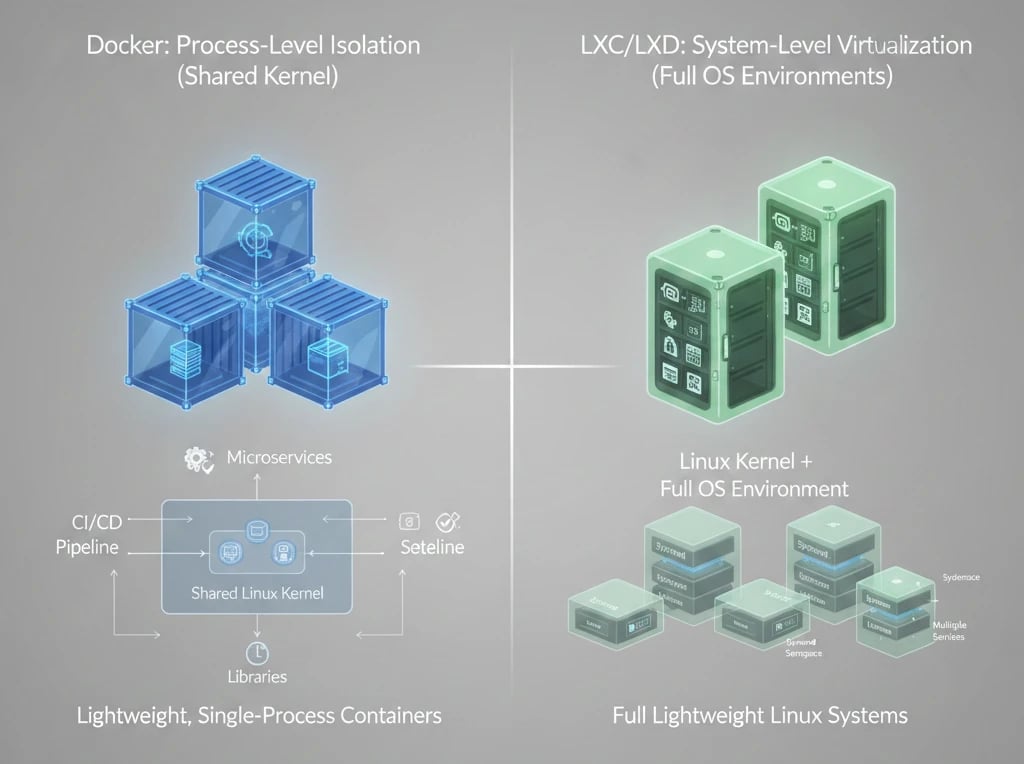
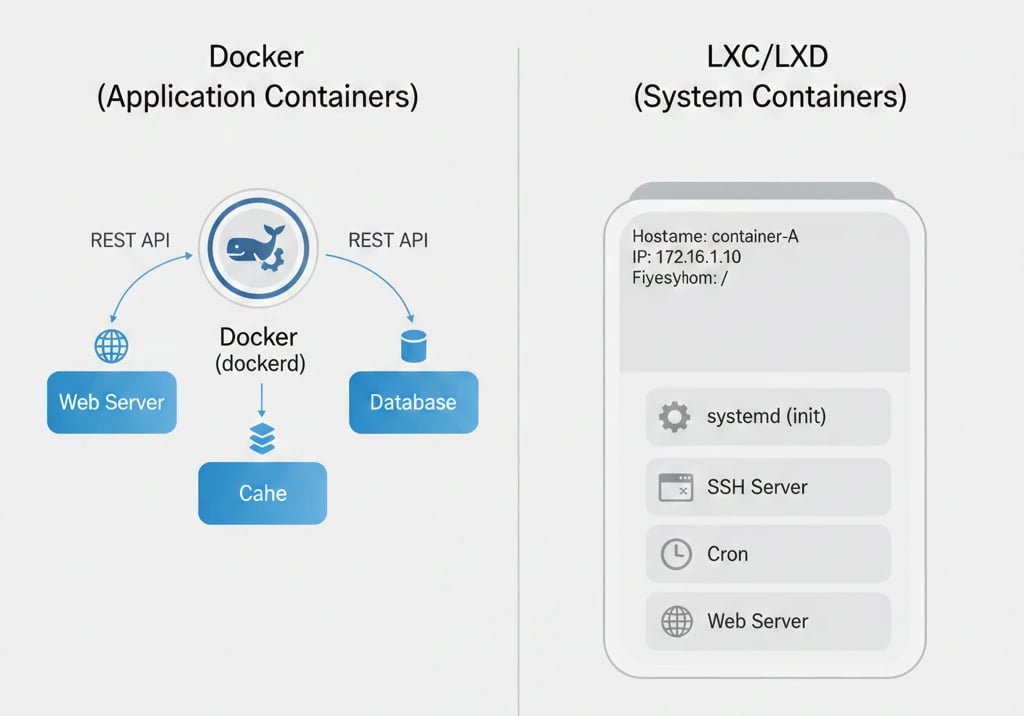
Docker was aimed at being a development and deployment platform when it was created. The main feature of Docker was isolating a single process or service along with all the dependencies it needed. By this method, Docker containers are by default the most suitable for stateless and ephemeral workloads. Isolation is done by Docker in user space, however, the host Linux kernel is still shared. The way the system is designed, it is a perfect tool for agile development, microservices architectures, and fast operations in CI/CD pipelines.
What is LXC/LXD?
LXC is an operating system–level virtualization technology, and LXD is the way that lets you have a complete Linux OS running inside a lightweight container. LXC is aimed to be a light virtual machine with a full init system (like systemd) controlling multiple services (like SSH, Cron, and web servers). Thus, it is a perfect solution for system administrators who want to have several different Linux systems running on a single host with very little overhead, and at the same time, need full system-level emulation.
You can deepen your understanding of containerization by exploring What is Docker in our comprehensive guide.
Key Architectural Differences
The major point to acknowledge first is that Docker and LXC/LXD are built on the same base. Both of these technologies depend on two fundamental Linux kernel features: Namespaces that isolate each container's environment by dividing PID, network, and filesystem, and cgroups that, for example, limit CPU and memory resource consumption. Nonetheless, they significantly differ in their process model and container structure.
Docker (Application Container)
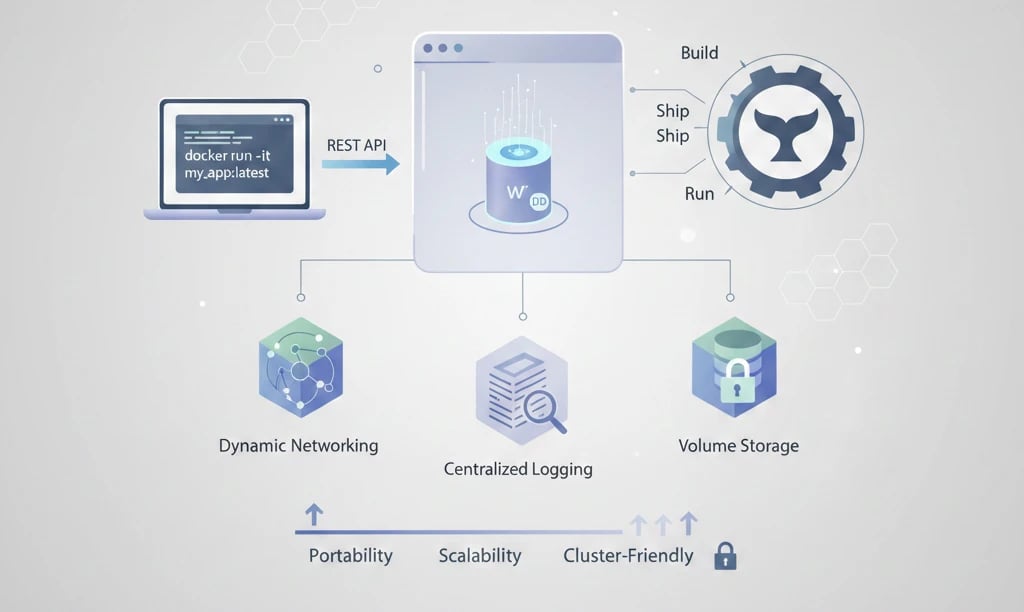
A Docker container is intended to have one main process only, for instance, a web server or a database engine. Docker implements a client–server architecture, which is mainly portable and simple. In case you run a command like docker run by CLI, it is actually a request to the Docker daemon (dockerd) that is sent via a REST API.
The daemon which plays the part of the system's core and is responsible for the container lifecycle management, including creation, execution, and monitoring, receives the command and performs the required operation.
The container management is simplified with such an architecture, and some of the key features like centralized logging, dynamic networking, and volume storage come as built-in functions. Therefore, Docker constitutes a complete ecosystem that covers the whole pipeline, starting from development to deployment. Docker is highly scalable, and its design is perfect for production environments using clusters.
LXC/LXD (System Container)
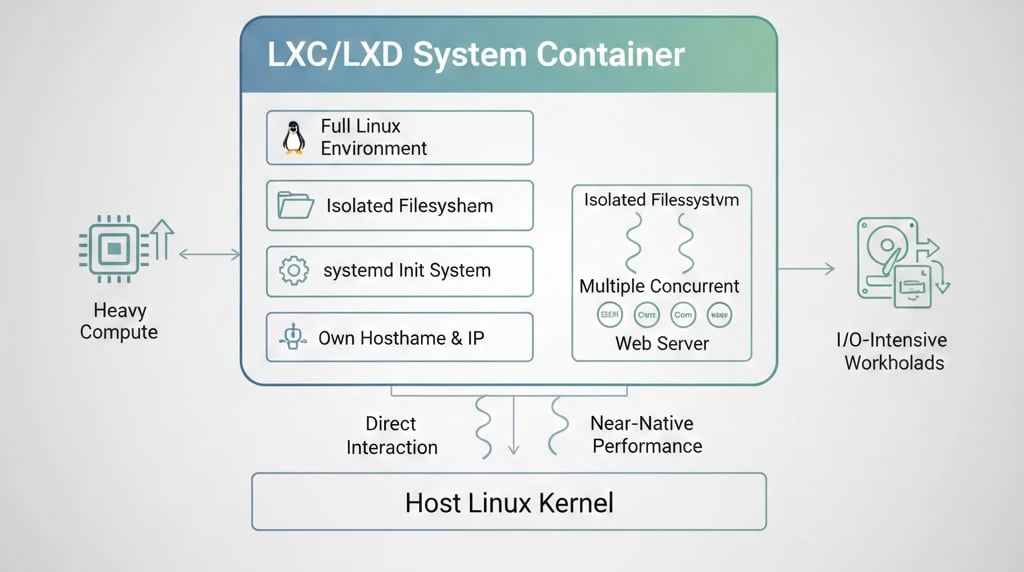
LXC/LXD containers offer a fully-fledged Linux environment. In comparison to Docker, they do not depend on a central daemon. These containers directly call Linux kernel APIs and come with a complete init system (for instance, Systemd), thus allowing services as well as processes to run concurrently. Hence, an LXC/LXD container can be considered as very similar to a lightweight virtual machine in terms of behavior.
The essential benefit is that a container can operate as a complete OS: it may have its own hostname, IP, isolated filesystem, init services, and even SSH. The given feature is quite useful in situations when a complete Linux environment is necessary.
Moreover, as LXC utilizes the host kernel, it is almost on par with bare-metal performance, which is the reason it is suitable for heavy compute or I/O-intensive workloads. On the other hand, because it has a lower abstraction level, one usually needs to be an advanced Linux user to be able to configure and manage LXC.
Below is a table showing the core differences between the two isolation models:
|
Key Feature |
Docker (Application Container) |
LXC/LXD (System Container) |
|
Primary Focus |
Running a single isolated application; ideal for microservices |
Providing a complete, manageable OS similar to a VPS |
|
Container Type |
Application Container |
System Container |
|
Architecture Model |
Client–server architecture with central daemon (dockerd) |
No central daemon; direct interaction with Linux kernel |
|
Container Contents |
Application + libraries + dependencies (minimalistic) |
Full rootfs; e.g., Ubuntu, Debian, or Alpine with systemd |
|
Portability |
Very high; runs on Linux, Windows, and macOS |
Lower; best compatibility on Linux only |
Docker became widely adopted by targeting developer platforms (such as Docker Desktop on Windows and macOS, which uses lightweight VMs), whereas LXC primarily remained in powerful Linux-native environments.
To understand how system containers compare to full virtualization, check out our guide on KVM vs LXC.
Feature-by-Feature Comparison
When choosing between tools, comparing operational features, security models, and resource efficiency is critical. So let us begin with a quick look at the feature differences between Docker and LXC.
|
Key Feature |
Docker (Application Container) |
LXC/LXD (System Container) |
|
State Management |
Stateless, ideal for fast and ephemeral scaling |
Stateful, ideal for persistent and long-running services |
|
Network Management |
Virtual networking with Bridge, NAT, Overlay (in Docker Swarm and Kubernetes) |
VM-like networking with tighter control, bridge and macvlan support |
|
Service Initialization |
No real init; runs a single application as PID 1 |
Full init system available (systemd, sysvinit) |
|
Resource Control |
Resource management via cgroups with limited granularity |
Precise control of CPU, RAM and I/O using cgroups v1/v2 |
|
Security Model |
Relies on seccomp, AppArmor and SELinux but dockerd has high privileges |
Stronger isolation; direct kernel capabilities and LXD security profiles |
|
Namespace Model |
PID, Network, Mount, UTS, IPC |
More complete support plus better handling of User Namespaces |
|
Rootless Support |
Full (Rootless Docker) |
Full (LXD unprivileged containers) |
|
Ecosystem and Tooling |
Very extensive (Compose, Swarm, Kubernetes) |
Suited for server management; deep integration with Proxmox and MAAS |
|
Common Use Cases |
Microservices, CI and CD, development environments, SaaS |
VPS hosting, legacy application migration, full-service workloads |
|
Execution Speed |
Very fast build and run due to layered architecture |
Fast but heavier since it runs a full OS |
|
Resource Consumption |
Low; only a single application runs |
Higher; due to init system and multiple services |
|
Kubernetes Support |
Yes; Docker uses containerd which is the K8s standard |
No; LXC/LXD is not designed for Kubernetes |
|
Complexity Level |
Simpler for development workflows |
More complex for system administration |
|
VM Replacement |
No, not a VM replacement |
Yes, a lightweight alternative to VMs |
If the table seems too brief, the following explanations will give you a clearer understanding.
Container Lifecycle Management
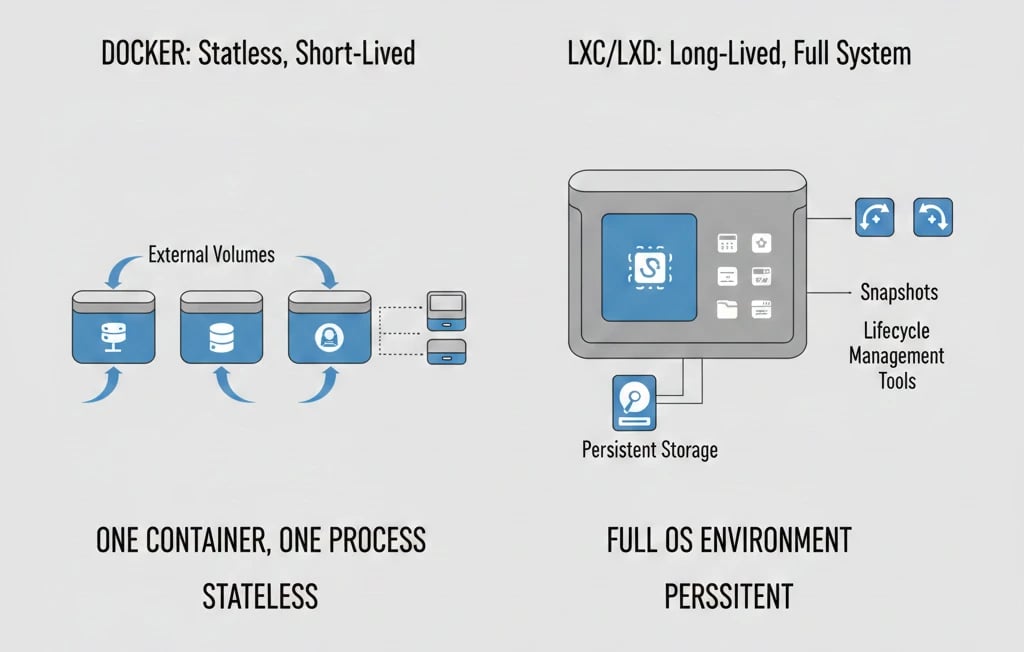
Docker is aligned with the philosophy of "one container, one process". While this facilitates orchestration, it implies that containers are by nature stateless and temporary. Any data that is to be retained must be explicitly directed to an external volume since Docker does not inherently support persistent data.
On the other hand, LXD and LXC are capable of running multiple processes and booting up a full system. LXD is naturally geared towards long-lived containers and has features for persistent data, snapshots, and advanced lifecycle operations. Therefore, it is perfect for embedding full application stacks within a single container.
Performance and Resource Efficiency
Due to its lightweight architecture and the fact that it extensively shares the host OS, Docker might be causing very little overhead. This is the main reason why it is highly efficient for small microservices that require fast startup and quick scaling.
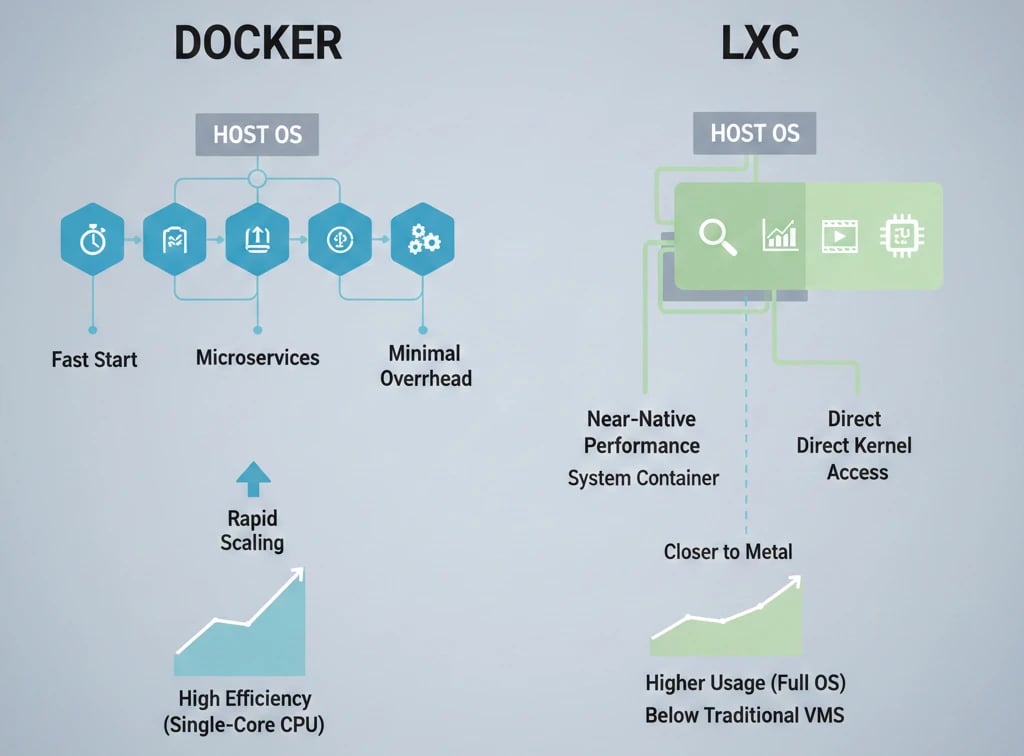
In a scenario that is CPU-bound and relies on a single core, Docker might even be able to run faster than LXD in terms of CPU and memory efficiency.
LXC is able to maintain a performance level that is almost at par with the native one thanks to its direct and close interaction with the host kernel. This is great for computationally intensive applications, for example, data analytics or video processing, as well as for workloads that require hardware direct access.
While LXC consumes more resources as compared to Docker, it is still much more resource-efficient than traditional virtual machines.
Storage and Networking Management
LXD offers not only substantially more powerful storage and networking features over bare-metal Docker but also is designed around a VM-like infrastructure. It is created with the enterprise-level storage management needs in perspective.LXD supports advanced backends like ZFS and Ceph, and provides integrated, customizable, and complex networking configurations. LXD also enables live migration (the process of moving a running container from one host to another) through the help of CRIU.
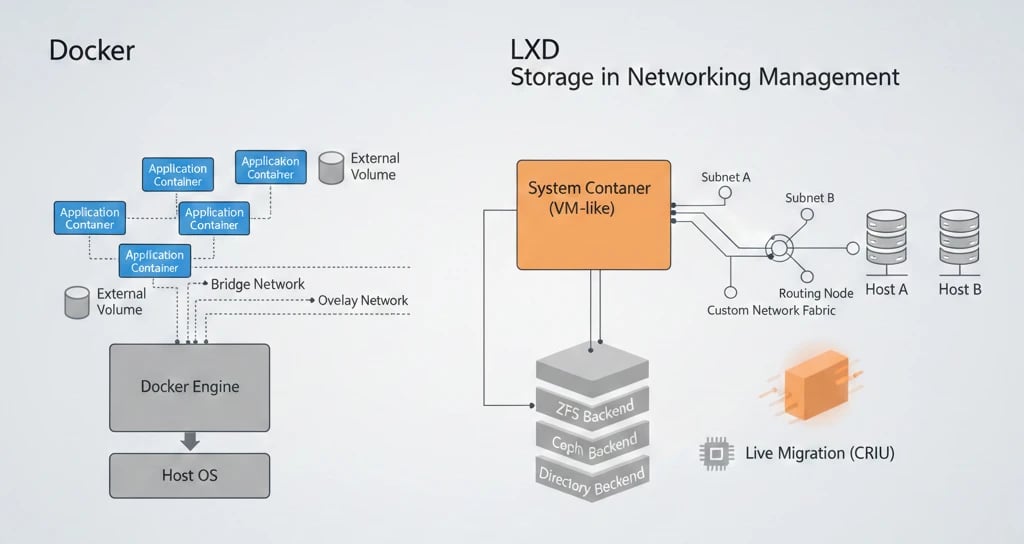
Docker relies heavily on volumes for data persistence in its storage model. As for networking, Docker comes with the native features such as Bridge Networks and Overlay Networks that facilitate communication between containers.
Security Considerations
Both have security models anchored on Linux kernel security features but, their security models are different due to their process models. Docker concentrates a lot on the aspect of running the container processes as non-root and cutting down the kernel capabilities. Isolation is achieved by the use of namespaces and cgroups and the system is designed in such a way that it would be very hard for a container to escape to the host and the container could be hacked.
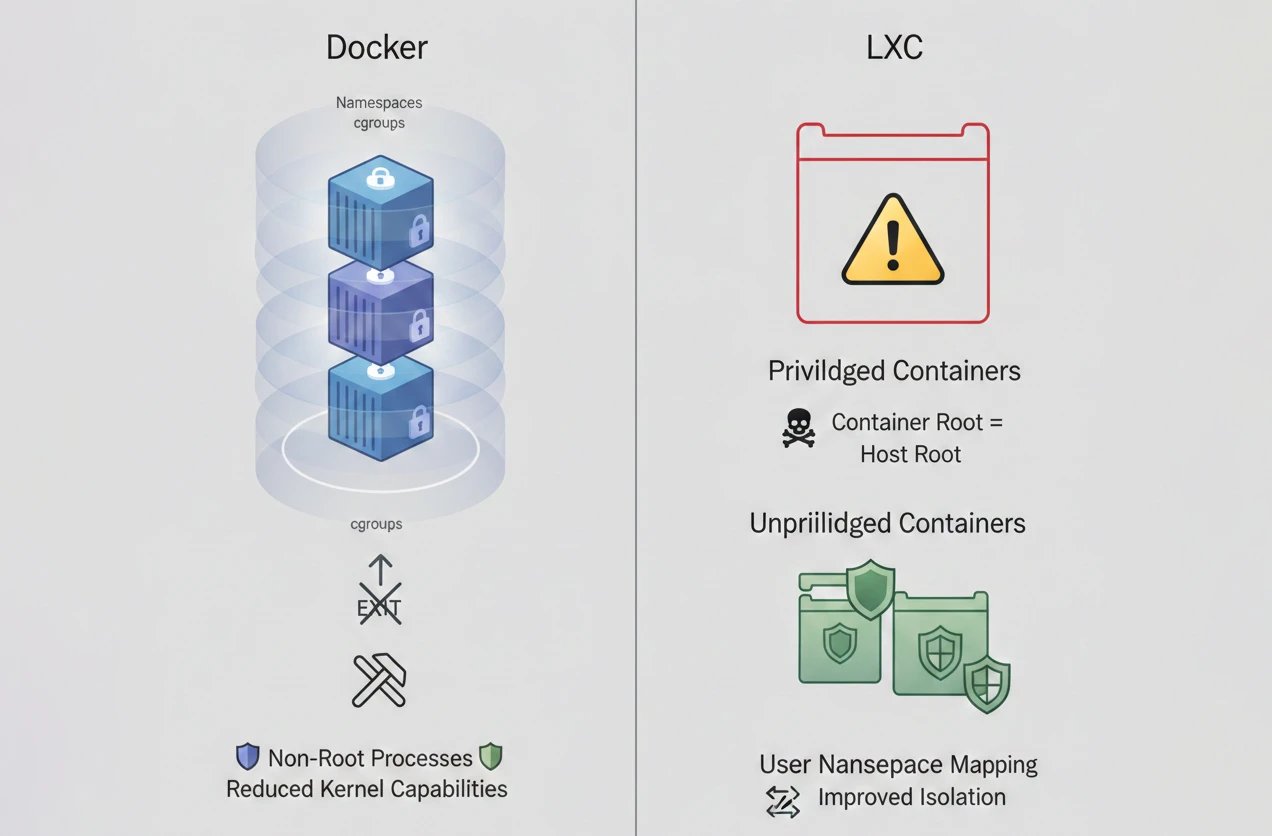
LXC distinguishes two types of containers, i.e., Privileged and Unprivileged ones.
-
As far as Privileged containers are concerned, they are quite unsafe because the root user inside the container is the same root on the host, and therefore this creates a serious security risk.
-
Unprivileged containers are the best practice model as user namespaces map the container root to a limited user on the host thus providing much stronger isolation.
The difference in security models comes from their design philosophies. Docker aims to avoid the need for root-level processes entirely, while LXC, being a full operating system environment, expects root processes to exist and must therefore enforce stronger namespace-based user and system isolation.
To deepen your Docker skills and practical knowledge, check out our curated list of Best Docker Tutorial Sources.
Ecosystem and Integration Support
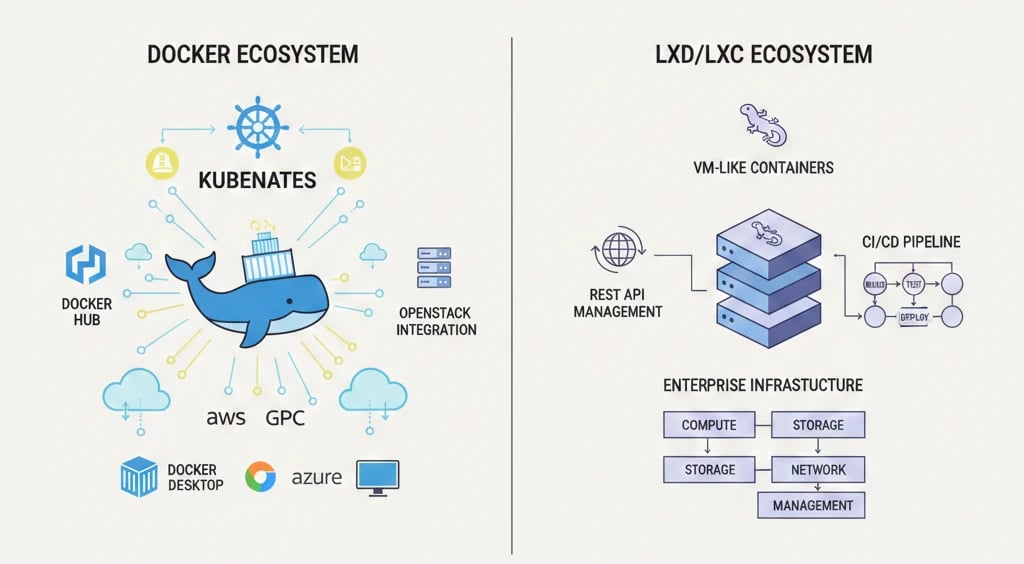
In general, choosing Docker means aligning with modern cloud-native development standards and the Kubernetes ecosystem, while LXD follows its own path in lightweight system-level virtualization. If your goal is to use industry-standard orchestration, Docker’s broad ecosystem typically outweighs LXD’s technical strengths, unless your workload is purely infrastructure-oriented and non-Kubernetes.
Docker’s Domain: Orchestration and Developer Tooling
Docker’s popularity since its introduction has been unmatched, primarily because it transformed the DevOps landscape.
-
Standardization with Kubernetes: Docker has become the operational standard for container orchestration and is compatible with platforms such as Kubernetes, ECS, and Mesos. This wide adoption makes it an essential part of modern cloud architectures.
-
Comprehensive developer tooling: Docker provides a complete toolchain including Docker Hub, Docker Desktop, and Docker Engine. Tools such as Docker Scout and Docker Debug enhance supply-chain security and streamline container troubleshooting, simplifying the full development-to-deployment lifecycle.
Docker accelerated collaboration and delivery workflows, which became more critical in the microservices era than the deeper system-level control offered by LXD. For this reason, Docker’s ecosystem evolved into the global standard.
LXC/LXD’s Domain: System-Oriented Environments and OpenStack
The LXC/LXD community is smaller and more specialized, consisting mostly of system administrators and advanced users.
-
Centralized, API-driven management: LXD is designed to manage containers similarly to virtual machines. With its REST API and clustering capabilities, LXD integrates well with VM and cloud management environments such as OpenStack. This makes it suitable for enterprise environments that require centralized control aligned with traditional virtualization infrastructure.
-
Stability and control: LXD remains a powerful solution for users who need efficient, scalable, and secure system-level containerization, and it continues to evolve as an open-source project.
A key point is that these two technologies can work together. Running Docker inside an LXD container (nesting) is fully supported and useful in test environments or CI/CD build pipelines that require complete isolation of build processes. To enable this capability, the security.nesting option in LXD must be set to true.
Use Cases and Recommendations
Your final decision should be based on your specific use case and architectural requirements.

When is Docker the right choice?
If your goal is to maximize development speed, portability, and application scalability, Docker is the undisputed choice.
-
Microservices and Stateless Applications: Docker is ideal for architectures built on small, independent microservices that require rapid deployment and horizontal scaling.
-
CI/CD (Continuous Integration/Continuous Deployment): Docker accelerates CI/CD pipelines by ensuring a standardized and repeatable development workflow.
And, If you need your application to run on any infrastructure (different clouds, local environments, or Windows/macOS via Docker Desktop), Docker’s standardization makes it the best option.
When is LXC/LXD the right choice?
LXC/LXD delivers the best performance in scenarios where the goal is to emulate a physical server or a traditional virtual machine with minimal overhead.
-
Desktop Virtualization (VDI): LXC is suitable for deploying VDI environments because it can run full operating systems with a much smaller footprint than traditional VMs, enabling efficient virtual desktop deployment.
-
Running Legacy Services or Multi-Service Systems: If you have older applications that rely on an init system (like Systemd), background process management, or multiple services running inside one environment, LXD is the best tool.
-
Native Performance and Hardware Access: Ideal for workloads requiring heavy computation (such as data analysis) or near-hardware access to Linux kernel features.
Also we recommend to Explore our detailed comparison on VM vs Docker to see which virtualization approach best fits your project needs.
Real-World Examples and CLI Breakdown
The user experience with these two tools at the command-line level (CLI) clearly reflects the difference in their underlying philosophies.

Launching a Web Server (Nginx) in Docker (Single-Process Model)
Docker expects the container to run only the main process. If you want to run Nginx in detached mode, you must ensure that the Nginx process stays in the foreground as PID 1 so the container does not exit. This is typically done with directives like daemon off; . Example of starting Nginx:
docker run -d -p 80:80 my_image nginx -g 'daemon off;'
If you use a command like service nginx start, the main process (PID 1) exits and the container stops because Docker assumes the job has finished. This demonstrates that Docker is centered on the stability of a single primary process.
Launching a Full Operating System in LXD (Multi-Process Model)
LXD, with simple commands, launches a full operating system similar to VM management tools. Practical steps:
1. Start the container: This command downloads the required image, creates a new container, and starts it immediately. lxc launch ubuntu:22.04 c1
2. View the list: lxc list
3. Enter the shell (run internal commands): You enter a full OS environment where init services are active: lxc exec c1 -- bash
LXD commands are designed similarly to VM management tools (such as virsh) and focus on managing the lifecycle of a full operating system, while Docker is designed for developers and fast application deployment.
You can see Operational Comparison of Key CLI Commands at below:
|
Operation |
Docker (Application-centric) |
LXC/LXD (System-centric) |
|
Start container |
docker run -d -p 80:80 my_image |
lxc launch ubuntu:22.04 c1 |
|
Execute inside |
docker exec -it <container> bash |
lxc exec c1 -- bash |
|
List instances |
docker ps -a |
lxc list |
|
Stop/Delete |
docker stop <id> / docker rm <id> |
lxc stop c1 / lxc delete c1 |
Check out our full guide on Docker vs Containerd to explore how these tools compare in real-world usage and CLI management.
Boost Your Workflows
Like any tool, the choice between Docker and LXC depends on your needs. Docker is an excellent option for rapid application development and deployment. On the other hand, LXC is more suitable when you need a full operating system environment or workloads that require heavy computational power.
Finally, if you want to run your container projects on a high-performance server with simple management, you can use our Docker VPS services at MonoVm for a fast and secure container experience. With our Docker VPS, you gain the flexibility to easily deploy and manage containers, simplifying your development, testing, and production workflows.







